Introducing GUFW the Uncomplicated Firewall GUI for Ubuntu Linux Hardy Heron!!
I just woke up this morning and found a great comment on my blog introducing me to a promising new project by marcoscostales called gufw and he has taken his time to create a .deb package for us all. This application looks promising and can only get better with our suggestions.
So far 1200 people on Ubuntu Brainstorm voted for an application like this, see here
Features: Enable/disable Firewall via 1 click access
Deny all inbound/outbound connections with 1 click
Allow all inbound/outbound connections with 1 click
A nice allow/deny drop down box.
Easily add/remove firewall rules
Block ping replies to show up as having a stealth/invisible ip on the lan/inet
Screens:
Download GuFw here
See here for updated packages
Double click the .deb file and click install.
You will find ufw with a nice shield icon via Applications->Internet->gufw
For support see here
Help improve this application by submitting bug reports and ideas here
News: Announcing GNOME Do 0.5: “The Fighting 0.5″
Article and pics via David Siegel's blog:
It has been 41 days since we released GNOME Do 0.4.2, and today I’m honored to present GNOME Do 0.5: “The Fighting 0.5″. Without further ado, here are the main improvements and new features, accompanied by plenty of sexy screenshots (click for larger images).
First off, the Open with… action has been re-enabled!
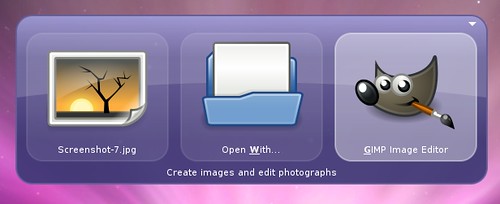
The biggest new feature in GNOME Do 0.5 is our new preferences window and plugin manager. You can now browse, download, install, and enable or disable all available plugins from right within Do thanks to Mono.Addins:
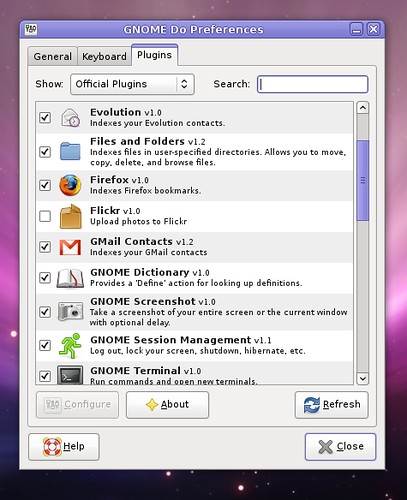
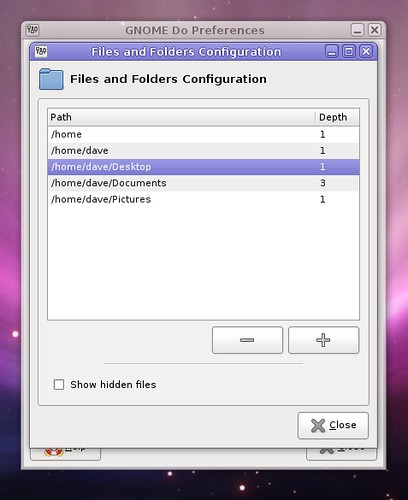
You can also visit a wiki page with information about each plugin, and you can do plugin-specific configuration. This means no more configuration files, and no more editing preferences through Configuration Editor (gconf). As an example, here is the configuration window for the Files and Folders plugin:
We’ve added a plugin category called “community plugins” that contains cutting-edge plugins written by many different contributors. If a developer were to write a great new GNOME Do plugin today, we could have it in the community plugins repository and available to Do users everywhere by tomorrow. That being said, community plugins are not rigorously screened or held to the same quality standards as official plugins, so users beware.
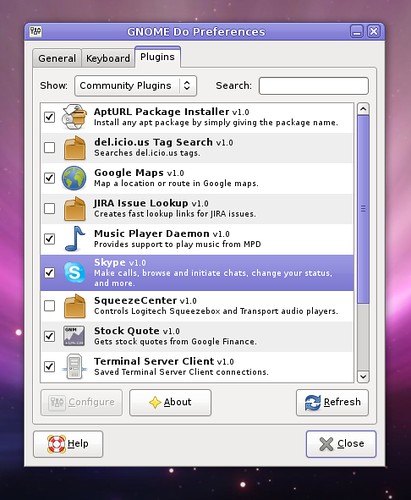
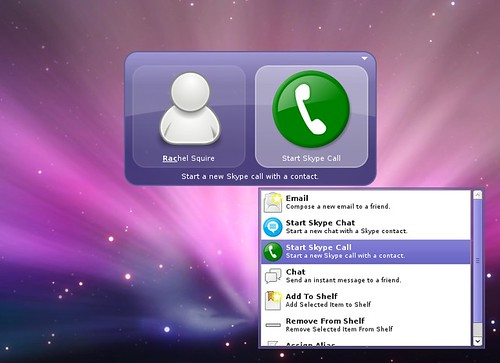
One of my favorite community plugins is the new Skype plugin, which allows you to make calls, initiate chats, change your status, and more. The Skype plugin is also fully integrated with Do’s contact system, so you can simply type a contact name, and then chose to send an instant message to that person with Pidgin, email them, or initiate a Skype chat or call:
There’s an awesome new plugin by Jason Smith called “WindowManager.” It lets you manipulate and rearrange windows on your desktop. You can focus, shade, minimize, maximize, tile, and cascade your windows. This plugin is so feature-packed, I don’t even know everything it does yet! Check out these screenshots, then try the plugin for yourself.

Minimize all Firefox windows.
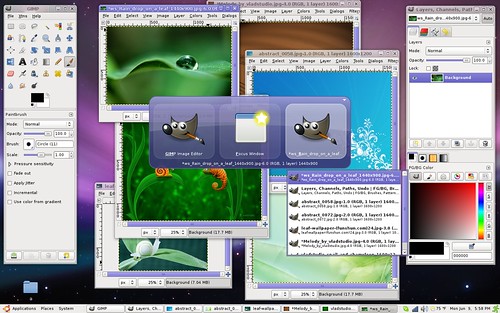
Bring a GIMP window into focus by searching for its name.
Alex Launi has done some amazing plugin work, making great contributions to the Twitter, File and Folders, and Pidgin plugins to name a few. He also wrote new Flickr, Gmail contacts, and Google Calendar plugins. Here’s a preview of his work:

Twitter plugin now supports replying to Twitter friends.
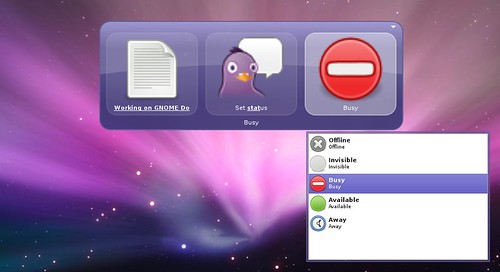
Set Pidgin status (also searches saved statuses).

Upload images to Flickr
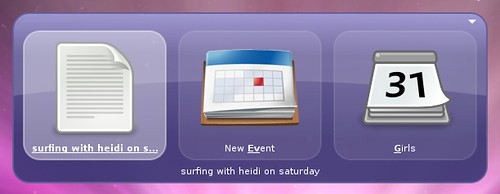
Search and create events on Google Calendar
These are only a few of the new features and improvements in GNOME Do 0.5. We’ve also fixed tons of bugs, and we’re going to have some intensive wiki-updating sessions over the next couple weeks to bring documentation up to speed. There are a few more changes that just barely missed the cut, so you can expect to see a 0.5.1 release within a few weeks. Special thanks to Alex Launi, Jason Smith, Chris Halse Rogers, Jorge Castro, Jason Imison, Jason Jones, Jacob Andreas, Guillaume Beland, Ken Simon, Mathieu Cadet, Rick Harding, and all the rest. Ubuntu users may get 0.5 packages from our Launchpad PPA, and you can find source packages on our downloads page.
Finally, GNOME Do is free software, and we work on Do because we love it. Do is free to use, but if you could spare a few hundred yen to help us cover hosting costs and other Do-related expenses, please click the ugly yellow donate button at the bottom of the page and we will be forever grateful. Thank you and enjoy!
Howto Install in Hardy Heron:
Add these sources via System->Administration->Software Sources->Third Party-> +Add:
deb http://ppa.launchpad.net/do-core/ubuntu hardy main
deb-src http://ppa.launchpad.net/do-core/ubuntu hardy main
Click here to install within Firefox or sudo apt-get install gnome-do via the command line
Howto: Install The Official Google Gadgets in Ubuntu Linux!
Via cnet:
Google Desktop has been available for some time now on Windows, Mac and Linux platforms. However, Google Gadgets — mini-applications that can be placed anywhere on the desktop — have, until now, only been available on Windows and Mac. Jim Zhuang, of Google's software engineering team, announced the first Linux version on Tuesday.
"Since releasing Google Desktop for Linux, we've added almost all of our most requested features, like 64-bit support and the ability to search applications and documents. All [but for] one major exception: Desktop Gadgets," wrote Zhuang on the company's open-source blog. "Gadget support is not just a single feature, but rather an entire platform for miniature applications. It's a complex undertaking, but we're now putting the finishing touches on the product."
Zhuang invited developers to view the source code for the entire project. "For Gadgets for Linux, we don't just want to simply release the final offering, but we also want to give everyone a chance to tinker with the code powering the gadgets," Zhuang wrote. "For this project, fostering a transparent and lively developer community is just as important as serving our users."
Google Gadgets for Linux are compatible with those written for Google Desktop for Windows and the "Universal Gadgets" on iGoogle. Therefore, according to the company, "a large library of existing gadgets [is] immediately available to Linux users, [and] gadget developers will benefit from a much larger potential user base without having to learn a new API".
The downloadable application includes the gadget library and a host program to allow users to run the gadgets on the desktop. Hosts are available for both GTK+ and Qt. The project is open sourced under the Apache License.
Howto Install:
Open System->Administration->Software Sources->Third Party repo's
Add these repo's:deb http://ppa.launchpad.net/googlegadgets/ubuntu hardy maindeb-src http://ppa.launchpad.net/googlegadgets/ubuntu hardy main
Now lets finally install shall we?
Click here after adding and refreshing the repository to install via one click or via the command line:sudo apt-get install google-gadgets
Press Alt-F2 and type in ggl-gtk
You autostart Google Gadgets for Linux by opening sessions via System->Preferences->Sessions
Then click +Add and input the fields like this:
Name:Google Gadgets
Command Line:sleep 10 ; ggl-gtk
Click ok and then make sure its check marked to startup
The Top Security Tools in the Ubuntu Repositories you may not know about with 1 click Installation!
Here is a collection of security tools that you should look through to add to your arsenal to help keep the peace on your pc/network or unleash war on others for whatever reason.
You can simply install these tools by clicking on the title within firefox in Ubuntu Hardy Heron.
Most of these are command line tools which need to be invoked via the Terminal:
Applications->Accessories->Terminal
If you need help with these tools, please read the manual via man "application" in the terminal, and feel free to comment if you need a little assistance or care to add to this growing list
Sniffers:
dsniff
Various tools to sniff network traffic for cleartext insecurities
This package contains several tools to listen to and create network traffic:
* arpspoof - Send out unrequested (and possibly forged) arp replies.
* dnsspoof - forge replies to arbitrary DNS address / pointer queries
on the Local Area Network.
* dsniff - password sniffer for several protocols.
* filesnarf - saves selected files sniffed from NFS traffic.
* macof - flood the local network with random MAC addresses.
* mailsnarf - sniffs mail on the LAN and stores it in mbox format.
* msgsnarf - record selected messages from different Instant Messengers.
* sshmitm - SSH monkey-in-the-middle. proxies and sniffs SSH traffic.
* sshow - SSH traffic analyser.
* tcpkill - kills specified in-progress TCP connections.
* tcpnice - slow down specified TCP connections via "active"
traffic shaping.
* urlsnarf - output selected URLs sniffed from HTTP traffic in CLF.
* webmitm - HTTP / HTTPS monkey-in-the-middle. transparently proxies.
* webspy - sends URLs sniffed from a client to your local browser
(requires libx11-6 installed).
Please do not abuse this software.
-
imsniff
Simple program to log Instant Messaging activity on the network
The imsniff program can be used to log IM activity on the network. It uses
libpcap to capture packets and analyzes them, logging conversation, contact
lists, etc.
Users connecting after imsniff is started can get pretty good results,
including complete contact lists and events (displaying a name change, for
example). Users already connected will be able to get the conversations, but
will miss the other information.
The only required parameter is the interface name to listen to. This can be
any interface that libpcap supports. A sample imsniff.conf.sample file is
included.
imsniff is beta software, for now, only MSN is supported. Others could follow.
Author: Carlos Fernandez
-
ksniffer
network traffic analyzer for KDE
KSniffer is a network traffic analyzer, or "sniffer" for KDE.
A sniffer is a tool used to capture packets from your network.
it detects network protocols like IP, TCP, UDP, ICMP and ARP.
-
nwatch
Network service detector
NWatch is a sniffer but can be conceptualized as a "passive port
scanner", in that it is only interested in IP traffic and it organizes
results as a port scanner would.
The advantage of this tool is that services that are open for a short
period of time can be detected with NWatch while successive nmap scans
will miss them. The disadvantage is that the service have to be actively
used to be detected.
-
scapy
Scapy is a powerful interactive packet manipulation tool, packet
generator, network scanner, network discovery, packet sniffer, etc. It
can for the moment replace hping, 85% of nmap, arpspoof, arp-sk, arping,
tcpdump, tethereal, p0f, ....
In scapy you define a set of packets, then it sends them, receives
answers, matches requests with answers and returns a list of packet couples
(request, answer) and a list of unmatched packets. This has the big advantage
over tools like nmap or hping that an answer is not reduced to
(open/closed/filtered), but is the whole packet.
Homepage: http://www.secdev.org/projects/scapy/
It was previously named scapy. This is a transitional package
so scapy users get python-scapy on upgrades. This package handles
scapy -> python-scapy. It can be safely removed.
-
Snort
Flexible Network Intrusion Detection System
Snort is a libpcap-based packet sniffer/logger which can be used as a
lightweight network intrusion detection system. It features rules
based logging and can perform content searching/matching in addition
to being used to detect a variety of other attacks and probes, such
as buffer overflows, stealth port scans, CGI attacks, SMB probes, and
much more. Snort has a real-time alerting capability, with alerts being
sent to syslog, a separate "alert" file, or even to a Windows computer
via Samba.
This package provides the plain-vanilla snort distribution and does not
provide database (available in snort-pgsql and snort-mysql) support.
-
tcpick
TCP stream sniffer and connection tracker
This libpcap-based textmode sniffer can:
* track, reassemble and reorder TCP streams
* save the captured flows in different files or display them in the terminal
* display all the stream on the terminal with different display modes like
hexdump, hexdump + ascii, only printable characters, raw mode, colorized
mode ...
* handle several network interface types, including ethernet cards and PPP
interfaces
-
Tshark
Wireshark network traffic analyzer (console interface)
Wireshark is a network traffic analyzer, or "sniffer", for Unix and
Unix-like operating systems. A sniffer is a tool used to capture
packets off the wire. Wireshark decodes numerous protocols (too many
to list).
This package provides the console version of wireshark, named
"tshark".
-
WireShark
network traffic analyzer
Wireshark is a network traffic analyzer, or "sniffer", for Unix and
Unix-like operating systems. A sniffer is a tool used to capture
packets off the wire. Wireshark decodes numerous protocols (too many
to list).
This package provides wireshark (the GTK+ version)
-
Last But not least for the sniffers is my personal fav:
Ettercap
Multipurpose sniffer/interceptor/logger for switched LAN
Ettercap supports active and passive dissection of many protocols
(even ciphered ones) and includes many feature for network and host
analysis.
Data injection in an established connection and filtering (substitute
or drop a packet) on the fly is also possible, keeping the connection
synchronized.
Many sniffing modes were implemented to give you a powerful and complete
sniffing suite. It's possible to sniff in four modes: IP Based, MAC Based,
ARP Based (full-duplex) and PublicARP Based (half-duplex).
It has the ability to check whether you are in a switched LAN or
not, and to use OS fingerprints (active or passive) to let you know the
geometry of the LAN.
Wireless Tools:
aircrack-ng
Grab the latest @ www.aircrack-ng.com
wireless WEP/WPA cracking utilities
aircrack-ng is an 802.11a/b/g WEP/WPA cracking program that can recover a
40-bit, 104-bit, 256-bit or 512-bit WEP key once enough encrypted packets have
been gathered. Also it can attack WPA1/2 networks with some advanced
methods or simply by brute force.
It implements the standard FMS attack along with some optimizations,
thus making the attack much faster compared to other WEP cracking tools.
It can also fully use a multiprocessor system to its full power in order
to speed up the cracking process.
aircrack-ng is a fork of aircrack, as that project has been stopped by
the upstream maintainer.
-
Kismet
Wireless 802.11b monitoring tool
Kismet is a 802.11b wireless network sniffer. It is capable of sniffing
using almost any supported wireless card using the Airo, HostAP, Wlan-NG,
and Orinoco (with a kernel patch) drivers.
Can make use of sox and festival to play audio alarms for network events
and speak out network summary on discovery. Optionally works with gpsd
to map scanning.
-
Prismstumbler
Wireless network sniffer
Prismstumbler is a packet sniffer for 802.11b wireless LANs.
-
SWScanner
Simple Wireless Scanner
SWScanner is a KDE application specially designed to make easy the whole
wardriving process, but also intended to facilitate many tasks related
to wireless networks. SWScanner is compatible with NetStumbler files and
supports GPS devices.
-
WEPLab
tool designed to break WEP keys
WepLab is a tool designed to teach how WEP works, what different
vulnerabilities it has, and how they can be used in practice to
break a WEP protected wireless network.
WepLab can dump network traffic, analyse it or crack the WEP key.
-
Portscanning:
NMAP
The Network Mapper
Nmap is a utility for network exploration or security auditing. It
supports ping scanning (determine which hosts are up), many port
scanning techniques, version detection (determine service protocols
and application versions listening behind ports), and TCP/IP
fingerprinting (remote host OS or device identification). Nmap also
offers flexible target and port specification, decoy/stealth scanning,
sunRPC scanning, and more. Most Unix and Windows platforms are
supported in both GUI and commandline modes. Several popular handheld
devices are also supported, including the Sharp Zaurus and the iPAQ.
-
PnScan
Multi threaded port scanner
Pnscan is a multi threaded port scanner that can scan a large network
very quickly. If does not have all the features that nmap have but
is much faster.
-
DoScan
port scanner for discovering services on large networks
doscan is a tool to discover TCP services on your network. It is
designed for scanning a single ports on a large network. doscan
contacts many hosts in parallel, using standard TCP sockets provided
by the operating system. It is possible to send strings to remote
hosts, and collect the banners they return.
There are better tools for scanning many ports on a small set of
hosts, for example nmap.
-
HPING3
Active Network Smashing Tool
hping3 is a network tool able to send custom ICMP/UDP/TCP packets and
to display target replies like ping does with ICMP replies. It handles
fragmentation and arbitrary packet body and size, and can be used to
transfer files under supported protocols. Using hping3, you can test
firewall rules, perform (spoofed) port scanning, test network
performance using different protocols, do path MTU discovery, perform
traceroute-like actions under different protocols, fingerprint remote
operating systems, audit TCP/IP stacks, etc. hping3 is scriptable
using the TCL language.
-
Paketto
Unusual TCP/IP testing tools
The Paketto Keiretsu is a collection of tools that use new and unusual
strategies for manipulating TCP/IP networks. scanrand is said to be
faster than nmap and more useful in some scenarios.
This package includes:
* scanrand, a very fast port, host, and network trace scanner
* minewt, a user space NAT/MAT (MAC Address Translation) gateway
* linkcat(lc), that provides direct access to the network (Level 2)
* paratrace, a "traceroute"-like tool using existing TCP connections
* phentropy, that plots a large data source onto a 3D matrix
-
Packit
Network Injection and Capture
Packit is a network auditing tool. Its value is derived from its ability
to customize, inject, monitor, and manipulate IP traffic. By allowing you
to define (spoof) nearly all TCP, UDP, ICMP, IP, ARP, RARP, and Ethernet
header options, Packit can be useful in testing firewalls, intrusion
detection systems, port scanning, simulating network traffic, and general
TCP/IP auditing. Packit is also an excellent tool for learning TCP/IP.
-
ScanSSH
get SSH server versions for an entire network
The ScanSSH protocol scanner scans a list of addresses and networks for
running SSH protocol servers and their version numbers. Version 2.0 adds
support for scanning arbitrary ports and specifically open proxies. The
ScanSSH protocol scanner supports random selection of IP addresses from
large network ranges and is useful for gathering statistics on the
deployment of SSH protocol servers in a company or the Internet as whole.
-
p0f
Passive OS fingerprinting tool
p0f performs passive OS detection based on SYN packets. Unlike nmap
and queso, p0f does recognition without sending any data.
Additionally, it is able to determine the distance to the remote
host, and can be used to determine the structure of a foreign or
local network. When running on the gateway of a network it is able
to gather huge amounts of data and provide useful statistics. On a
user-end computer it could be used as powerful IDS add-on. p0f
supports full tcpdump-style filtering expressions, and has an
extensible and detailed fingerprinting database.
-
Misc Tools:
TCPTraceroute
A traceroute implementation using TCP packets
The more traditional traceroute(8) sends out either UDP or ICMP ECHO
packets with a TTL of one, and increments the TTL until the destination
has been reached. By printing the gateways that generate ICMP time
exceeded messages along the way, it is able to determine the path packets
are taking to reach the destination.
The problem is that with the widespread use of firewalls on the modern
Internet, many of the packets that traceroute(8) sends out end up being
filtered, making it impossible to completely trace the path to the
destination. However, in many cases, these firewalls will permit inbound
TCP packets to specific ports that hosts sitting behind the firewall are
listening for connections on. By sending out TCP SYN packets instead of
UDP or ICMP ECHO packets, tcptraceroute is able to bypass the most common
firewall filters.
Traceroute
Traces the route taken by packets over an IPv4/IPv6 network
The traceroute utility displays the route used by IP packets on their way to a
specified network (or Internet) host. Traceroute displays the IP number and
host name (if possible) of the machines along the route taken by the packets.
Traceroute is used as a network debugging tool. If you're having network
connectivity problems, traceroute will show you where the trouble is coming
from along the route.
Install traceroute if you need a tool for diagnosing network connectivity
problems.
Homepage:
Whois
the GNU whois client
This is a new whois (RFC 3912) client rewritten from scratch.
It is inspired from and compatible with the usual BSD and RIPE whois(1)
programs.
It is intelligent and can automatically select the appropriate whois
server for most queries.
The package also contains mkpasswd, a simple front end to crypt(3).
-
Rootkit Detection:
Chkrootkit
Checks for signs of rootkits on the local system
chkrootkit identifies whether the target computer is infected with a rootkit.
Some of the rootkits that chkrootkit identifies are:
1. lrk3, lrk4, lrk5, lrk6 (and some variants);
2. Solaris rootkit;
3. FreeBSD rootkit;
4. t0rn (including latest variant);
5. Ambient's Rootkit for Linux (ARK);
6. Ramen Worm;
7. rh[67]-shaper;
8. RSHA;
9. Romanian rootkit;
10. RK17;
11. Lion Worm;
12. Adore Worm.
Please note that this is not a definitive test, it does not ensure that the
target has not been cracked. In addition to running chkrootkit, one should
perform more specific tests.
-
RkHunter
rootkit, backdoor, sniffer and exploit scanner
Rootkit Hunter scans systems for known and unknown rootkits,
backdoors, sniffers and exploits.
It checks for:
- MD5 hash changes;
- files commonly created by rootkits;
- executables with anomalous file permissions;
- suspicious strings in kernel modules;
- hidden files in system directories;
and can optionally scan within files.
Using rkhunter alone does not guarantee that a system is not
compromised. Running additional tests, such as chkrootkit, is
recommended.
-
UnHide
Forensic tool to find hidden processes and ports
Unhide is a forensic tool to find processes and TCP/UDP ports hidden by
rootkits, Linux kernel modules or by other techniques. It includes two
utilities: unhide and unhide-tcp.
unhide detects hidden processes using three techniques:
- comparing the output of /proc and /bin/ps
- comparing the information gathered from /bin/ps with the one gathered
from system calls (syscall scanning)
- full scan of the process ID space (PIDs bruteforcing)
unhide-tcp identifies TCP/UDP ports that are listening but are not listed in
/bin/netstat through brute forcing of all TCP/UDP ports available.
This package can be used by rkhunter in its daily scans.
-
Secure Erase:
wipe
Secure file deletion
Recovery of supposedly erased data from magnetic media is easier than what many
people would like to believe. A technique called Magnetic Force Microscopy
(MFM) allows any moderately funded opponent to recover the last two or three
layers of data written to disk. Wipe repeatedly writes special patterns to the
files to be destroyed, using the fsync() call and/or the O_SYNC bit to force
disk access.
-
Undelete/Recovery:
Foremost
Forensics application to recover data
This is a console program to recover files based on their headers and
footers for forensics purposes.
Foremost can work on disk image files, such as those generated by dd,
Safeback, Encase, etc, or directly on a drive. The headers and footers
are specified by a configuration file, so you can pick and choose which
headers you want to look for.
-
e2undel
Undelete utility for the ext2 file system
Interactive console tool to recover the data of deleted files on
an ext2 file system under Linux. It does not require knowledge
about how ext2 file systems works and should be usable by
most people.
This tools searches all inodes marked as deleted on a file system and
lists them as sorted by owner and time of deletion. Additionally,
it gives you the file size and tries to determine the file type in
the way file(1) does. If you did not just delete a whole bunch of
files with a 'rm -r *', this information should be helpful to find
out which of the deleted files you would like to recover.
E2undel will not work on ext3 (journaling) filesystems.
Homepage: http://e2undel.sourceforge.net
-
Recover
Undelete files on ext2 partitions
Recover automates some steps as described in the ext2-undeletion
howto. This means it seeks all the deleted inodes on your hard drive
with debugfs. When all the inodes are indexed, recover asks you some
questions about the deleted file. These questions are:
* Hard disk device name
* Year of deletion
* Month of deletion
* Weekday of deletion
* First/Last possible day of month
* Min/Max possible file size
* Min/Max possible deletion hour
* Min/Max possible deletion minute
* User ID of the deleted file
* A text string the file included (can be ignored)
If recover found any fitting inodes, it asks to give a directory name
and dumps the inodes into the directory. Finally it asks you if you
want to filter the inodes again (in case you typed some wrong
answers).
Note that recover works only with ext2 filesystems - it does not support
ext3.
http://recover.sourceforge.net/linux/recover/
-
Port Scan Detection:
PSAD
The Port Scan Attack Detector
PSAD is a collection of four lightweight system daemons written in
Perl and in C that is designed to work with Linux firewalling code
(iptables in the 2.4.x kernels, and ipchains in the 2.2.x kernels)
to detect port scans. It features a set of highly configurable danger
thresholds (with sensible defaults provided), verbose alert messages
that include the source, destination, scanned port range, begin and
end times, tcp flags and corresponding nmap options (Linux 2.4.x
kernels only), reverse DNS info, email alerting, and automatic
blocking of offending ip addresses via dynamic configuration of
ipchains/iptables firewall rulesets.
In addition, for the 2.4.x kernels psad incorporates many
of the tcp signatures included in Snort to detect highly suspect scans
for:
* various backdoor programs (e.g. EvilFTP, GirlFriend, SubSeven)
* DDoS tools (mstream, shaft)
* advanced port scans (syn, fin, xmas) such as those made with nmap
Homepage: http://www.cipherdyne.org/
-
PortSentry
Portscan detection daemon
PortSentry has the ability to detect portscans(including stealth scans) on
the network interfaces of your machine. Upon alarm it can block the
attacker via hosts.deny, dropped route or firewall rule. It is part of the
Abacus program suite.
Note: If you have no idea what a port/stealth scan is, It's recommended to
have a look at http://sf.net/projects/sentrytools/ before installing this
package. Otherwise you might easily block hosts you'd better not (e.g. your
NFS-server, name-server, etc.).
-
Snort
Flexible Network Intrusion Detection System
Snort is a libpcap-based packet sniffer/logger which can be used as a
lightweight network intrusion detection system. It features rules
based logging and can perform content searching/matching in addition
to being used to detect a variety of other attacks and probes, such
as buffer overflows, stealth port scans, CGI attacks, SMB probes, and
much more. Snort has a real-time alerting capability, with alerts being
sent to syslog, a separate "alert" file, or even to a Windows computer
via Samba.
This package provides the plain-vanilla snort distribution and does not
provide database (available in snort-pgsql and snort-mysql) support.
-
Privilege escalation detection:
Ninja
Ninja is a privilege escalation detection and prevention
system for GNU/Linux hosts. While running, it will monitor
process activity on the local host, and keep track of all
processes running as root. If a process is spawned with
UID or GID zero (root), ninja will log necessary information
about this process, and optionally kill the process
if it was spawned by an unauthorized user.
A "magic" group can be specified, allowing members of this
group to run any setuid/setgid root executable.
Individual executables can be whitelisted. Ninja uses a
fine grained whitelist that lets you whitelist executables
on a group and/or user basis. This can be used to allow
specific groups or individual users access to setuid/setgid
root programs, such as su(1) and passwd(1).
Homepage: http://forkbomb.org/ninja
Filesystem Integrity:
Aide
Advanced Intrusion Detection Environment - static binary
AIDE is an intrusion detection system that detects changes to files on
the local system. It creates a database from the regular expression rules
that it finds from the config file. Once this database is initialized
it can be used to verify the integrity of the files. It has several
message digest algorithms (md5, sha1, rmd160, tiger, haval, etc.) that are
used to check the integrity of the file. More algorithms can be added
with relative ease. All of the usual file attributes can also be checked
for inconsistencies.
This package contains the statically linked binary for "normal"
systems.
You will almost certainly want to tweak the configuration file in
/etc/aide/aide.conf or drop your own config snippets into
/etc/aide/aide.conf.d.
Upstream URL: http://sourceforge.net/projects/aide
-
Integrit
A file integrity verification program
Integrit helps you determine whether an intruder has modified your
system. Without the use of integrit, a sysadmin wouldn't know if the
programs used for investigating the system are trojan horses or not.
Integrit works by creating a database that is a snapshot of the most
essential parts of the system. You put the database somewhere safe,
and then later you can use it to make sure that no one has made any
illicit modifications to your file system.
Integrit's key features are the small memory footprint, the design
with unattended use in mind, intuitive cascading rulesets for the
paths listed in the configuration file, the possibility of XML or
human-readable output, and simultaneous checks and updates.
See http://integrit.sourceforge.net/ for more information.
-
Debsums
Verify installed package files against MD5 checksums.
debsums can verify the integrity of installed package files against
MD5 checksums installed by the package, or generated from a .deb
archive.
-
Fcheck
IDS filesystem baseline integrity checker
The fcheck utility is an IDS (Intrusion Detection System)
which can be used to monitor changes to any given filesystem.
Essentially, fcheck has the ability to monitor directories, files
or complete filesystems for any additions, deletions, and modifications.
It is configurable to exclude active log files, and can be ran as often
as needed from the command line or cron making it extremely difficult to
circumvent.
-
SamHain
Data integrity and host intrusion alert system
Samhain is an integrity checker and host intrusion detection system that
can be used on single hosts as well as large, UNIX-based networks.
It supports central monitoring as well as powerful (and new) stealth
features to run undetected on memory using steganography.
Main features
* Complete integrity check
+ uses cryptographic checksums of files to detect
modifications,
+ can find rogue SUID executables anywhere on disk, and
* Centralized monitoring
+ native support for logging to a central server via encrypted
and authenticated connections
* Tamper resistance
+ database and configuration files can be signed
+ logfile entries and e-mail reports are signed
+ support for stealth operation
Homepage: http://la-samhna.de/samhain/index.html
-
SleuthKit
Tools for forensics analysis
The Sleuth Kit (previously known as TASK) is a collection of UNIX-based
command line file system and media management forensic analysis tools.
The file system tools allow you to examine file systems of a suspect
computer in a non-intrusive fashion. Because the tools do not rely on
the operating system to process the file systems, deleted and hidden
content is shown.
The media management tools allow you to examine the layout of disks and
other media. The Sleuth Kit supports DOS partitions, BSD partitions
(disk labels), Mac partitions, and Sun slices (Volume Table of
Contents). With these tools, you can identify where partitions are
located and extract them so that they can be analyzed with file system
analysis tools.
When performing a complete analysis of a system, we all know that
command line tools can become tedious. The Autopsy Forensic Browser is
a graphical interface to the tools in The Sleuth Kit, which allows you
to more easily conduct an investigation. Autopsy provides case
management, image integrity, keyword searching, and other automated
operations.
The Sleuth Kit's upstream homepage can be found at
http://www.sleuthkit.org/sleuthkit/.
-
Stealth
A stealthy File Integrity Checker
The STEALTH program performs File Integrity Checks on (remote) clients. It
differs from other File Integrity Checkers by not requiring baseline
integrity data to be kept on either write-only media or in the client's file
system. In fact, client's will contain hardly any indication at all that they
are being monitored, thus improving the stealthiness of the integrity scans.
STEALTH uses standard available software to perform file integrity checks
(like find(1) and md5sum(1)). Using individualized policy files, it is highly
adaptable to the specific requirements of its clients.
In production environments STEALTH should be run from an isolated computer
(called the `STEALTH monitor'). In optimal configurations the STEALTH
monitor should be a computer not accepting incoming connections. The account
used to connect to its clients does not have to be `root': usually
read-access to the client's file system is enough to perform a full integrity
check. Instead of using `root' a more restrictive administrative or
ordinary account might offer all requirements for the desired integrity
check.
STEALTH itself must communicate with the computers it should monitor. It is
essential that this communication is secure, and STEALTH configurations will
therefore normally specify SSH as the command-shell to use to connect to its
clients. STEALTH may be configured so as to use but one SSH connection per
client, even if integrity scans are to be performed repeatedly. Apart from
this, the STEALTH monitor might be allowed to send e-mail to remote clients
system's maintainers.
STEALTH-runs itself may start randomly within specified intervals. The
resulting unpredicability of STEALTH-runs further increases STEALTH's
stealthiness.
STEALTH's acronym is expanded to `Ssh-based Trust Enforcement Acquired
through a Locally Trusted Host': the client's trust is enforced, the locally
trusted host is the STEALTH monitor.
-
TripWire
file and directory integrity checker
Tripwire is a tool that aids system administrators and users in
monitoring a designated set of files for any changes. Used with
system files on a regular (e.g., daily) basis, Tripwire can notify
system administrators of corrupted or tampered files, so damage
control measures can be taken in a timely manner.
Have anything else worth mentioning? Please leave a comment
Introducing the Unofficial Google command shell!

Do you love google search like I do? And have love for the terminal as well? I just stumbled across this interesting and fun new site called GooSH that streamlines searching google in a nice unix shell interface.
Check it out Here
Here are your command Options:guest@goosh.org:/web> help
help
command aliases parameters function
web (search,s,w) [keywords] google web search
lucky (l) [keywords] go directly to first result
images (image,i) [keywords] google image search
wiki (wikipedia) [keywords] wikipedia search
clear (c) clear the screen
help (man,h,?) [command] displays help text
news (n) [keywords] google news search
blogs (blog,b) [keywords] google blog search
feeds (feed,f) [keywords] google feed search
open (o) < url > open url in new window
go (g) < url > open url
more (m) get more results
in (site) < url >
load < extension_url > load an extension
video (videos,v) [keywords] google video search
read (rss,r) < url > read feed of url
place (places,map,p) [address] google maps search
lang
addengine add goosh to firefox search box
translate (trans,t) [lang1] [lang2] < words > google translation
guest@goosh.org:/web>







